
A PRIMER ON THE ONGOING ORGANIZED CRIME SYNDICATE OF JEFFREY EPSTEIN'S FAILED BILLIONAIRE EXPERIMENT IN THE UNITED STATES, THE "COMMONWEALTH", AND IN THE EUROPEAN UNION
UpRights News has published a number of articles on what it is like to be U.S. law enforcement, witnesses, victims, university professors, whistleblowers, activists, and/or journalists investigating the sprawling ongoing organized crimes of the ongoing crime syndicate of Jeffrey Epstein, now being investigated from many different angles, from an international law perspective, a federal investigation perspective, a state, and a county investigation perspective(s), and from criminal and civil perspectives, as the number of the different billionaires named as clients, financiers, and/or associates of Jeffrey Epstein grows every year.
We provide access to his client book and flight logs in some of our articles, and in some of our other articles, investigative journalists like us have elucidated secret meetings between many of the big tech billionaires and Jeffrey Epstein, and/or "financing" arrangements and meetings, all of which came after he was convicted of prostitution with a child he sex trafficked.
Again, we do all of this as the founder of UpRights News was a male victim of Jeffrey Epstein, and an "insider" to the global elite enabling him, obstructing for him, financing him, overtly furthering and/or expanding, and/or using his child sex trafficking services.
Across our series of articles we have been able to prove that the most harmful criminal conspiracies harming Americans and our brothers and sisters in Jeffrey Epstein's UK and EU royal countries, at least for the last 20 years, were harmed by the clients, financiers, friends, and associates of Jeffrey Epstein, who was groomed at Dalton private school for children, by the father of Republican William Barr, who RICO obstructed justice for at least two different treason conspiracies, the Iran Contra treason conspiracy, and the Russia-Trump-GOP-Brexit treason conspiracy, allowing Jeffrey Epstein's David Koch's Federalist Society to install 6/9 GOP SCOTUS justices, who then sold our government to the failed billionaire experiment of Jeffrey Epstein's crime syndicate, and who have collectively been RICO obstructing justice for Republicans and the failed billionaire experiment of Jeffrey Epstein ever since, including but not limited to dismantling, distorting, ignoring, and mischaracterizing the laws, regulations, and funding that would have otherwise prevented and/or removed all of the same.
THE VICIOUS CYCLE OF GOVERNMENT CONTRACTS, CAMPAIGN CONTRIBUTIONS, AND REPUBLICANS
As specified across many of our different news articles at UpRights News, a vicious of ongoing bribery and corruption exists whereby the failed billionaire experiment of Jeffrey Epstein finances the Republican Party candidates from the top to the bottom of the government, who then stand a better chance of taking public offices, often illegally, who then provide multibillion dollar contracts to the failed billionaire experiment of Jeffrey Epstein, who then reinvest in the cycling by financing more Republicans into power.
As part of this cycle is the stealing of elections, gerrymandering elections, stealing ballots, stealing voting machines, elections fraud, massive misinformation campaigns leading up to elections, and/or other similar organized crime measures to allow the pedophile class of America and those they can deceive to hand power over the government to the organized crime syndicate of Jeffrey Epstein and Russia's GOP, in the context Putin is an accused sex trafficker of children by the ICC.
More simply, some of the wealthiest people in the world are pedophiles and/or pedophile-files, and they use their ill-got wealth to unlawfully seize power to expand their ongoing organized crimes and syndicate (largely operating as government employees), and to continuously obstruct justice for as much of the same as possible, and to buy their way out of jail time, almost always, with few notable exceptions.
As our previous reporting has elucidated, the pedophile crime syndicate of Jeffrey Epstein literally controls most of the communications infrastructure of the United States, often regulated by those they "engineer" into office, and they collectively control most of the large social media sites, and most of the largest news channels, and most of the largest ad targeting and data scooping companies, and they control most of the largest email account providers, and the largest website hosting services -- which collectively make up most of the largest intelligence network infrastructure of the United States, the Commonwealth, and/or the European Union, who share intelligence as to whoever might be investigating their ongoing organized crime syndicate.
As our articles on Jeffrey Epstein's David Koch's-financed Donor's "Trust", and their financing of GOP operatives' Turning Point USA and Project Veritas have proven, along with the related NSO conduct that is known, and also connected to the treason crimes of Jeffrey Epstein's UK royals' SCL Group's Cambridge Analytica, Jeffrey Epstein's Mark Zuckerberg's Facebook, and/or others -- the organized crime syndicate of Jeffrey Epstein has weaponized the largest social media sites, communications infrastructure, ad targeting marketing and data scooping companies, email companies, artificial intelligence companies, website hosting sites, and the like, to not just further their crimes against children, but to weaponize the same as an early warning system to alert them into who might be investigating them for which of their ongoing organized criminal conspiracies, and once those targets are elucidated, then they become the target of stalking, cyberstalking, cyberwarfare, cyberterrorism, cyberattacks, computer fraud, wire fraud, conversion, criminal harassment, retaliation, websites and email accounts or their content destroyed, altered, disappeared, and/or compromised, but not limited to the same.
THE ONGOING CYBERSTALKING, CYBERATTACKS, CYBERTERRORISM, CYBERWARFARE, CONVERSION, CRIMINAL HARASSMENT, AND RETALIATION AGAINST INVESTIGATIVE JOURNALISM AT UPRIGHTS NEWS
To illustrate what it is like to be an investigative journalist, activist, university faculty member, victim, whistleblower and/or U.S. law enforcement investigating the ongoing organized crimes of Jeffrey Epstein's failed billionaire experiment and their proxies -- in this context that they mostly control the communications infrastructure, social media accounts, marketing, ad targeting, news, email, and website building accounts -- we have decided to start publishing every time we are subjected to cyberbullying, cyberwarefare, cyberterrorism, cyberattacks, criminal harassment, retaliation, and/or the conversion of our computers, network, devices, accounts, and the like -- so that others can come to understand what it is like for us all trying to protect the rest of you from this ongoing organized crime syndicate through our investigations.
The following are just the most recent examples, most of them from today, and where we estimate we have hundreds of examples like this, but will begin by illustrating with the most recent examples, and then just update this article every time we are cyberattacked or denied services.
At 9:46AM today, we experienced a denial of service attack preventing us from changing a file name, below.
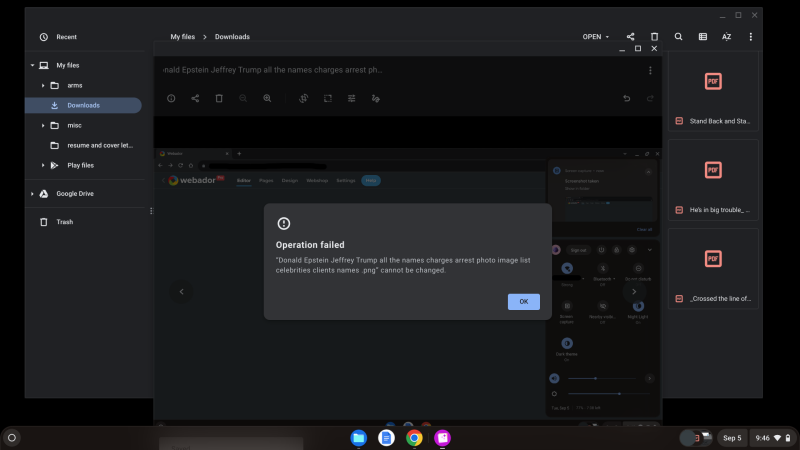
Here's this web page that refused to load after a minute to day. The time stamp in the bottom


Here's more of the same, but here a failure to load a website development block, which normally takes a second or two to load. Note that across the next two images that three minutes later, the page is still struggling to load, despite a strong internet signal, and yet again, normally takes seconds to load.


Here's another error message a minute later, specifying "something went wrong", despite a strong internet connection.

At 8:49AM today, we experienced a denial of service attack preventing us from accessing another company, and yet we have a strong signal to Jeffrey Epstein's named AT&T company in his black book, and we are working on a Google operating system, and where both of the Google founders have been linked to Jeffrey Epstein, and at least one of them has been subpoenaed by the Attorney General of the U.S. Virgin Islands over ties to Jeffrey Epstein. We have blacked out the URL and network names below as a security measure.

At 6:42AM today, we experienced a denial of service attack preventing us from accessing our server. We have blacked out the URL and network names as a security measure.

As a good cyber practice for those being stalked and harassed, we regularly delete our cookies and browsing data, but in that process we discovered that our devices are visiting many more websites than we are actually visiting, which is conversion or theft of our private property used by others who need our computer to visit sites we haven't visited, and we don't know what sites they are visiting with our internet devices, and they are downloading software onto our computers, which is another reason we clear out the same, and why we asked the federal authorities to monitor some of our online accounts and activity, to not later be accused of whatever these others are doing with our devices in this concealed manner.

We will try and dig up some more recent examples of all of the same, and the following other types of cyberterrorism we have experienced, for example, but not limited to the same, our computers have also let us know that others are using currently using our files, and so we can't have access to our own files, and our computers have also let us know that the only network we have access to has been disconnected, and that our computer has been linked to someone else's network, so some pretty smoking gun evidence here -- again where our goal is to differentiate between criminal conspiracies and frivolous ones, and where frivolous ones can't produce evidence -- which what we continuously produce, to prove the undisputed pattern.
We have also seen small windows or pop-up black boxes appear for a moment and then disappear, and sometimes are login pages look enormously different, and then return to the login page we are used to later.
Sometimes "ghost print" can be found on our desktop, that we can't click on nor deleted, which is just there. Other times, a ghost and paused "play button" appears out of nowhere.
We know from websites that track the same that almost all of our email accounts have been hacked -- along with almost all of the email accounts of our family members. We have experienced our email accounts and website being totally disappeared from the internet and access, despite paying for the same in the same year, and we have experience at least one website domain put up for sale by GoDaddy, also linked to Jeffrey Epstein's crime syndicate and/or their network.
We have also experienced errors in transferring files, and some of our files have been corrupted and won't open, and others were supposed to be PDF files, and within the image view of our files, we accidentally discovered Linux executable files (malevolent software that replaced our pdf file), so that if the same was ever opened a very likely harmful computer code would start. We lose about a computer a year to cyberattacks, and so it isn't easy for U.S. law enforcement, journalists, university professors, whistleblowers, activists, victims, or anyone to investigate Jeffrey Epstein's organized crime syndicate, because they largely own, control, and share the intelligence, communications, news, social media, email, and marketing infrastructure, to serve as (1) an early warning system and obstruction of justice weapon for those investigating them, (2) to further their crimes against children and those investigating them, and (3) to be able to influence others with misinformation that they are the heroes and victims and those investigating them are the radical villains -- as an ongoing crime syndicate linked to child sex crimes would want to do and need to do in order to avoid prosecution and to be able to further their ongoing crimes.
We have experienced changes made in our emails or website pages that weren't there when we sent or published a web page. We have had at least one article disappeared on the alleged brutal rape crimes of Jeffrey Epstein's Leon Black against a child that had both Down Syndrome and autism, who he allegedly brutally raped and sodomized with objects causing her to bleed, allegedly sex trafficked to him by Jeffrey Epstein, and where one of our investigative journalists worked for Leon Black but was cyberattacked, cyberbullied, and cyberterrorized out of the company owned by Leon Black, so consistent in that manner.
Also interesting, at the time that Leon Black's company was terrorizing one of our current journalists, Leon Black and other members of Jeffrey Epstein's crime syndicate who had harmed our journalist had met around the time our journalist was retaliated against and harassed out of employment by Leon Black's company, and for the second time, and where the first time our journalist was wrongfully terminated for researching the ongoing organized crime syndicate of Jeffrey Epstein, which included those Leon Black met with prior to running our journalist out of working for him -- per the published calendar of Leon Black and/or Epstein -- which proposed that they were supposed to meet and/or did meet together at these key or relevant times.
Here's another attack on our ability to access our server from yesterday, at 1:44PM, while writing an article on how the moral relativism of Nietzsche is what gave rise to the Powell Memo, Citizen's United bribery and corruption by SCOTUS, and to Trump's, Republicans', Jeffrey Epstein's, and corporate rape and enslavement culture in a "fuck your feelings" manner, sugar coated with plenty of references to altruist Jesus, God, and the like, despite them embracing the total opposite teachings and values of Jesus.
Again, all of this happening on a Google operating system, using a Google account, and using AT&T network, in the context that both Google founders and AT&T have been named in the client book or black book of child rapist Jeffrey Epstein, or in the case of the Google founders, linked to secret dinners with him and other California tech company leaders, after he convicted of prostitution with a child he sex trafficked.

Here's some obstruction of justice into our investigation into a very small minority of local law enforcement likely linked to the child sex trafficking crimes of Jeffrey Epstein and/or Russia's GOP, who have made us regular targets of dive-bombing our operations below the lawful altitude, while accelerating towards our operations to the top flight speed, after flying way off course to beeline to our operations, sometimes flying off course in the total opposite direction than the pilot intended by as much as 60 miles, requiring this small group of the same pilots and/or vehicles to then have to waste taxpayer funds to backtrack to where they were headed after terrorizing our operations and investigations into their ongoing organized crimes with Russia, the GOP, and/or Trump orbit.
This here proves a criminal conspiracy, because at least two parties overtly further the stalking and terrorism, and cyberstalking and cyberterrorism, in order to threaten our operations with a deadly weapon (an aircraft accelerating and point towards us at maximum flight speed flying below the legal altitude and then pulling up at the last minute to avoid crashing into our operations, with planes and choppers, some the size of commercial airliners, and we operate nowhere near an airport, nor do we operate between any local airports, requiring the pilots to fly off course to reach us, which they have to do on the front end, on the way to us, during their flight, and/or on the back end towards the end of their flight, as otherwise it would be hard for them to randomly fly over us, and where we discount this behavior with at least one flight per year for every pilot may be random.
All of the same is then often concealed by denial of service attacks, as the one found below, as we investigate on free online radars who is terrorizing our operations, and it is almost always the same vehicles and/or pilots, and where we live along the West Coast hate corridor per groups that track the hate groups, mostly along a (not so) Proud Boys hate corridor, and where we have at least 3 indicted insurrectionists living close to our operations, and have linked at least several of our harassers based out of McCellan Park to both Trump visiting with and financing the same with taxpayer funds, and separately linking the same to a local hate group, and separately linking them to insurrectionists and separately linking them to Sacramento GOP.

Here is one of many examples of our network being "changed" and yet we only pay for and connect to a single network, and so that is the only network we are connected to, and so we simply can't change networks, an impossibility, but others engaged in conversion of our private property, our computing devices, our routers, our modems, our firewalls, our internet provider, our accounts, our operating system, and/or our computing devices, specifically Jeffrey Epstein's AT&T and Google, and/or others, would be able to engage in wire fraud, computer fraud, cyberterrorism, cyberwarfare, cyberbullying, cyberharassment, identity fraud, terrorism to aid, comfort, and/or adhere to Russia and/or agents of Russia, and would be able to unlawfully take control of our computers, operating systems, routers, accounts, and the like, to be able affect the change in networks, which is otherwise impossible for us to affect. So here's a smoking gun for all of the same, or in legal terms, evidence beyond a reasonable doubt, because we simply don't have another network to change to, and so someone else has clearly changed our network to another network, resulting in this error message.

Below is a website link to evidence that the FBI investigated Jeffrey Epstein's Trump and his family (also named in Jeffrey Epstein's black book of clients, money launderers, financiers, and/or associates), for the Trump family's ties to communists and communist parties in Eastern Europe. Within about a week of us using evidence from this Microsoft website, this article was scrubbed from the internet, in the context that Jeffrey Epstein's Bill Gates is who founded and/or helps lead Microsoft.
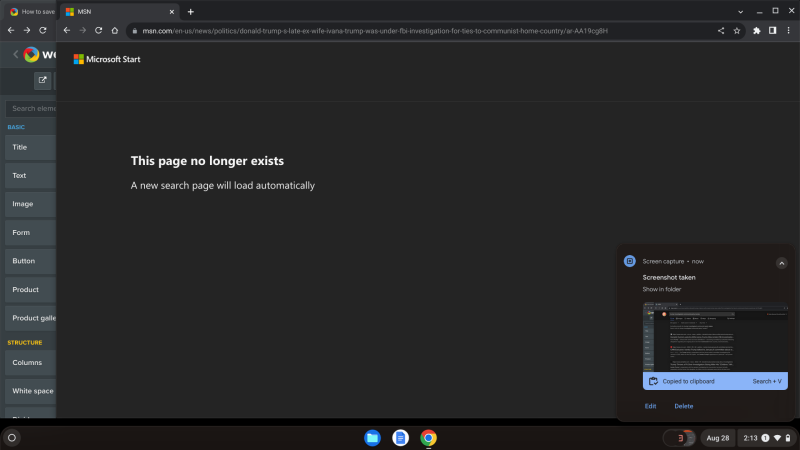
Here's a link to the FBI evidence that Jeffrey Epstein's Bill Gates, Jeffrey Epstein's Donald Trump, Jeffrey Epstein's Trump family, and/or others don't want you to learn about, while Jeffrey Epstein's most radical client, money launderer, and/or associate -- Donald Trump -- defensively projects he is the target of radical Marxists, communists, and/or socialists. If someone attacks the link, the URL to the same is found below, as are print screens of the evidence they don't want others to see.

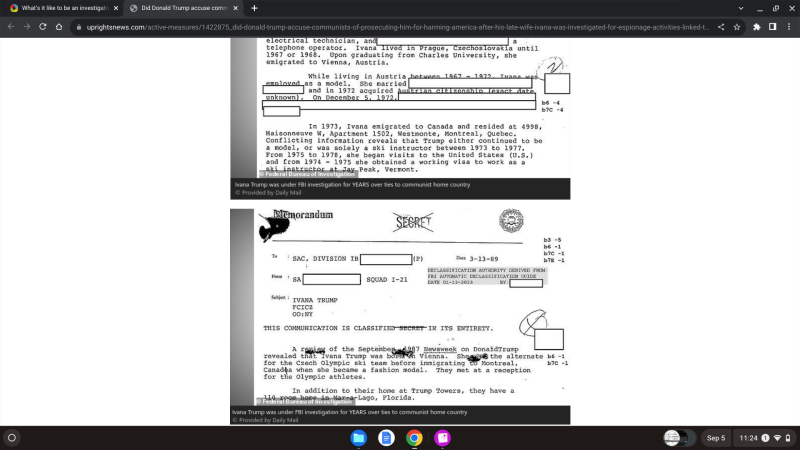
So this is what it is like for U.S. law enforcement, university professors, whistleblowers, activists, lawmakers, victims, and/or investigative journalists to investigate the ongoing organized crime syndicate of Jeffrey Epstein, who just like socialists, communists, terrorists, and organized crime, "share" their ill-got wealth and power to (1) keep their ongoing organized criminal conspiracies overtly going, and (2) to obstruct justice into investigations into any of the same by stalking, cyberstalking, cyberterrorism, cyberwarefare, and/or other ongoing organized crimes -- as ongoing organized crime, terrorists, traitors, and corrupted public offices would and have to in order to evade investigation, prosecution, liability, seizure of all of their assets, and/or the death penalty.
SOURCES AND ATTRIBUTES
[1] https://unsplash.com/@pacd_photography
As with every article published by, distributed, and/or edited by UpRights News, this article is also subject to the legal disclaimer below.

